Argument Injection Hammer Burp Suite Extension
I wrote a short blog post describing a Burp Suite extension that I developed here. This is just a repost originally hosted on the NCC Group research page…
Argument Injection Hammer is an extension for the intercepting proxy Burp Suite. I wrote the extension in order to enhance the ability of the proxy to detect argument injection and manipulation vulnerabilities in web applications.
The extension contains payloads that can detect argument injection and manipulation vulnerabilities associated with common Linux commands using both in-band detection techniques and timing-based detection techniques. Additionally, the extension also supports limited brute forcing of short argument flags.
Background
A web application is vulnerable to argument injection when untrusted inputs are passed as arguments when executing a specific command. An attacker can manipulate the arguments passed to the process to trigger either an arbitrary file write, arbitrary file read, or OS command injection depending on the supported arguments of the command and how the command is executed. Argument injection should not be confused with OS command injection in which it is possible to use shell metacharacters to force the target application to execute additional arbitrary OS commands.
Argument injection vulnerabilities are more common in Java applications that use the Runtime.exec method to execute commands based on user input since the command is not passed to a shell interpreter. Consider the following Java code snippet.
Runtime.getRuntime().exec("find /tmp -name " + taintedVariable);
While we cannot use shell metacharacters to inject in additional OS commands, we can abuse the application by providing additional arguments that the find command understands such as the exec argument.
* -exec id ;
To understand why we are unable to use shell metacharacters it is worth reviewing the underlying syscalls called by the Java application when the Runtime.exec method is invoked using the strace command. Lets examine a simple call to execute the echo command in a Java program.
Runtime.getRuntime().exec("/bin/echo hello");
By using strace we can see that execve is called and that the echo command is invoked directly, since the first execve argument is the filename of the program to be executed and the second argument is an array of arguments.
90655 execve("/bin/echo", ["/bin/echo", "hello"], 0x7ffe04dd1da0 /* 53 vars */ <unfinished ...>
Given that the /bin/echo program is executed directly without the use of a shell interpreter when using the Runtime.exec method, if we control the middle, or final, portion of the string passed to Runtime.exec method then argument injection or manipulation is possible, but traditional OS command injection is not possible. Now consider the commonly used system function in PHP.
<?php
system("/bin/echo hello");
?>
Again using strace we can see that the execve syscall is called, but this time the echo command is invoked indirectly via /bin/sh.
95288 execve("/bin/sh", ["sh", "-c", "/bin/echo hello"], 0x5650f09dfe70 /* 53 vars */ <unfinished ...>
Given that the /bin/echo program is executed indirectly via a shell interpreter, if we control any part of the string passed to the system function then OS command injection is possible since we can use shell metacharacters such as ; or | to force the application to execute additional OS commands. Note that PHP developers will often escape shell metacharacters within user input via the escapeshellcmd function to prevent OS command injection, but argument injection would still be possible. Alternatively, a developer could use the escapeshellarg function to escape quote characters in order to prevent argument injection, but argument manipulation might still be possible. Ultimately, developers must perform sufficient input validation on program inputs received from any external components to prevent OS command injection, argument injection, or argument manipulation attacks.
While it is more common to find OS command injection vulnerabilities in web applications, security researchers have demonstrated the danger of argument injection or manipulation vulnerabilities in recent years as developers have shifted to using safer API calls or escaping of shell metacharacters. Security researchers from Sogeti ESEC documented that passing arbitrary arguments to the sendmail command can lead to arbitrary file reads and writes, which can lead to remote code execution in a web application. David Golunski expanded upon Sogeti ESEC’s research and documented critical vulnerabilities in popular email libraries such as PHPMailer, Zend-mail, and SwiftMailer. Recently, Kacper Szurek demonstrated an argument manipulation attack against the GitList web application, which can lead to the execution of arbitary commands by abusing git’s –open-files-in-pager argument, and Chris Lyne demonstrated an argument injection attack against the Nagios XI network monitoring software, which can lead to an arbitrary file write by abusing curl’s –output argument.
Given the danger of argument injection and manipulation attacks, it is important that penetration testers have access to dynamic analysis tools that can help automate the detection of these types of vulnerabilities especially when the target application’s source code is unavailable for review.
Usage
The extension can be added into Burp Suite via the Extender tab. Once added, a number of new active scanning checks will be performed when using the Scanner. For example, the following screenshot shows an issue in which an attacker can control arguments passed to the zip command by an example vulnerable web application.
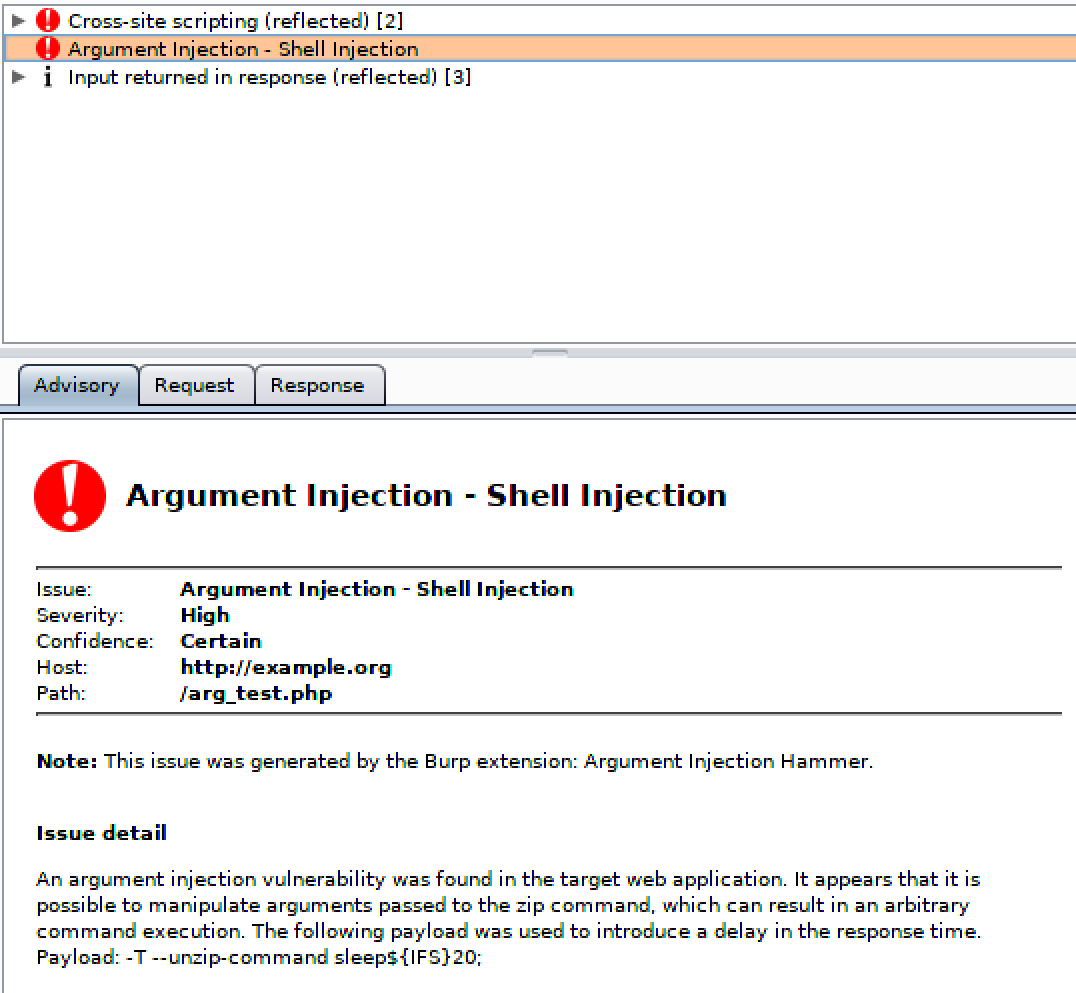
Note that by default the extension will not brute-force short argument flags, but this feature can be enabled via the extension’s tab. When this feature is enabled, the extension will brute-force short argument flags (-a, -b, -c, -d, etc.) in order to find argument injection issues that result in arbitary file reads as opposed to relying solely on known dangerous argument flags such as -exec, -e, --to-command, or --unzip-command.
Conclusion
I wrote the Argument Injection Hammer extension for Burp Suite in order to automate the hunt for argument injection vulnerabilities in web applications and web services by sending specific payloads that will either trigger a file read or write that is observable in a HTTP response or by sending payloads that will introduce a detectable delay in the arrival of the HTTP response. The extension currently focuses on payloads that are specific to Linux commands, but I plan to update the extension with payloads associated with Windows commands after additional research.